



Simply enter the website URL and get insights on recommendations, data breaches and more.
All ratings ever done are visible in the CyberRank Directory. You may also choose to publish your rating for more visibility in the IISRI® Directory.
Need Third Party Supply monitoring? CyberRank offers various intervals to simplify labor intensive vendor assessments.
CyberRank honours the best rated daily in the Top Rank. You can also filter by branch or country.
Yes, CyberRank performs a thorough analysis of DNS records and Autonomous System Numbers (ASN) to identify an organization‘s digital footprint.
Yes, even if a company restricts DNS queries, CyberRank can still discover most subdomains using advanced scanning techniques and historical data.
Yes, we conduct reverse DNS lookups and maintain a directory that links IP addresses to organizations, even when no DNS entry exists.
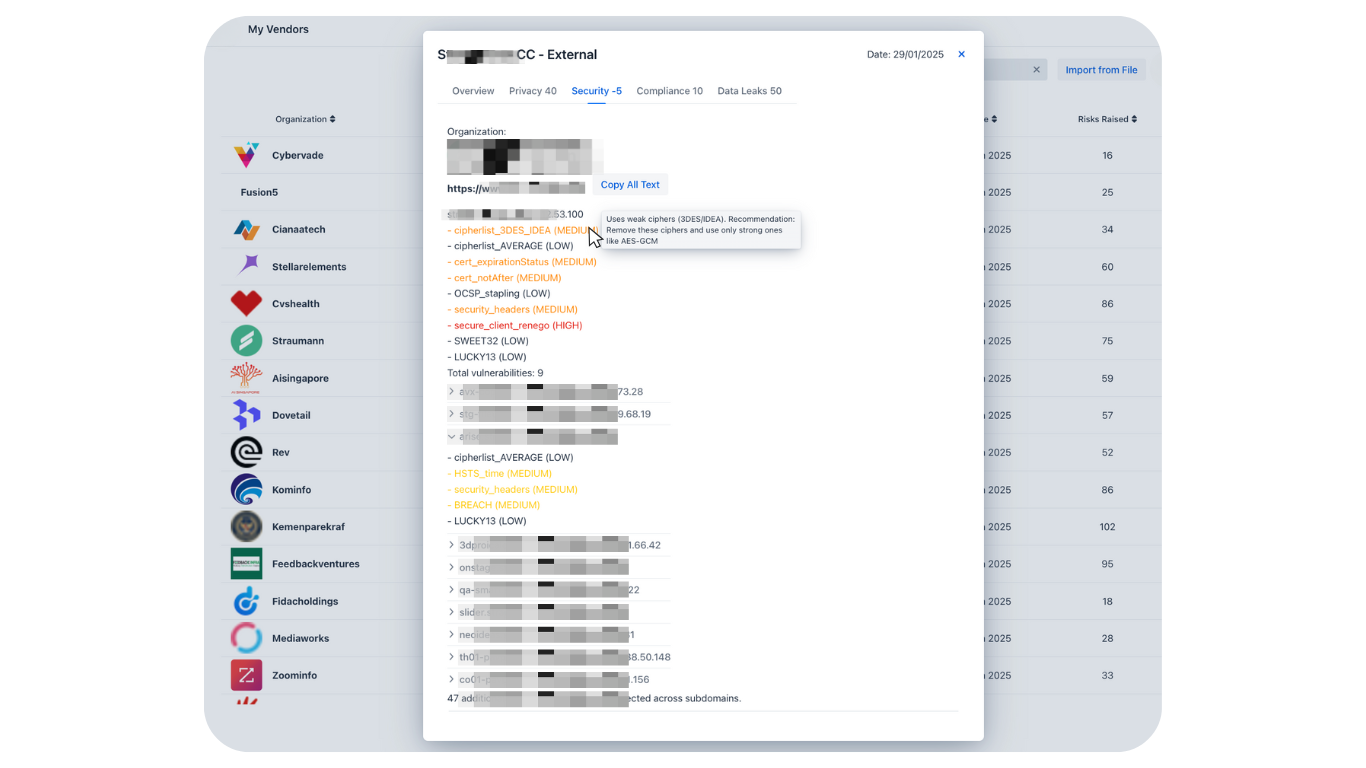

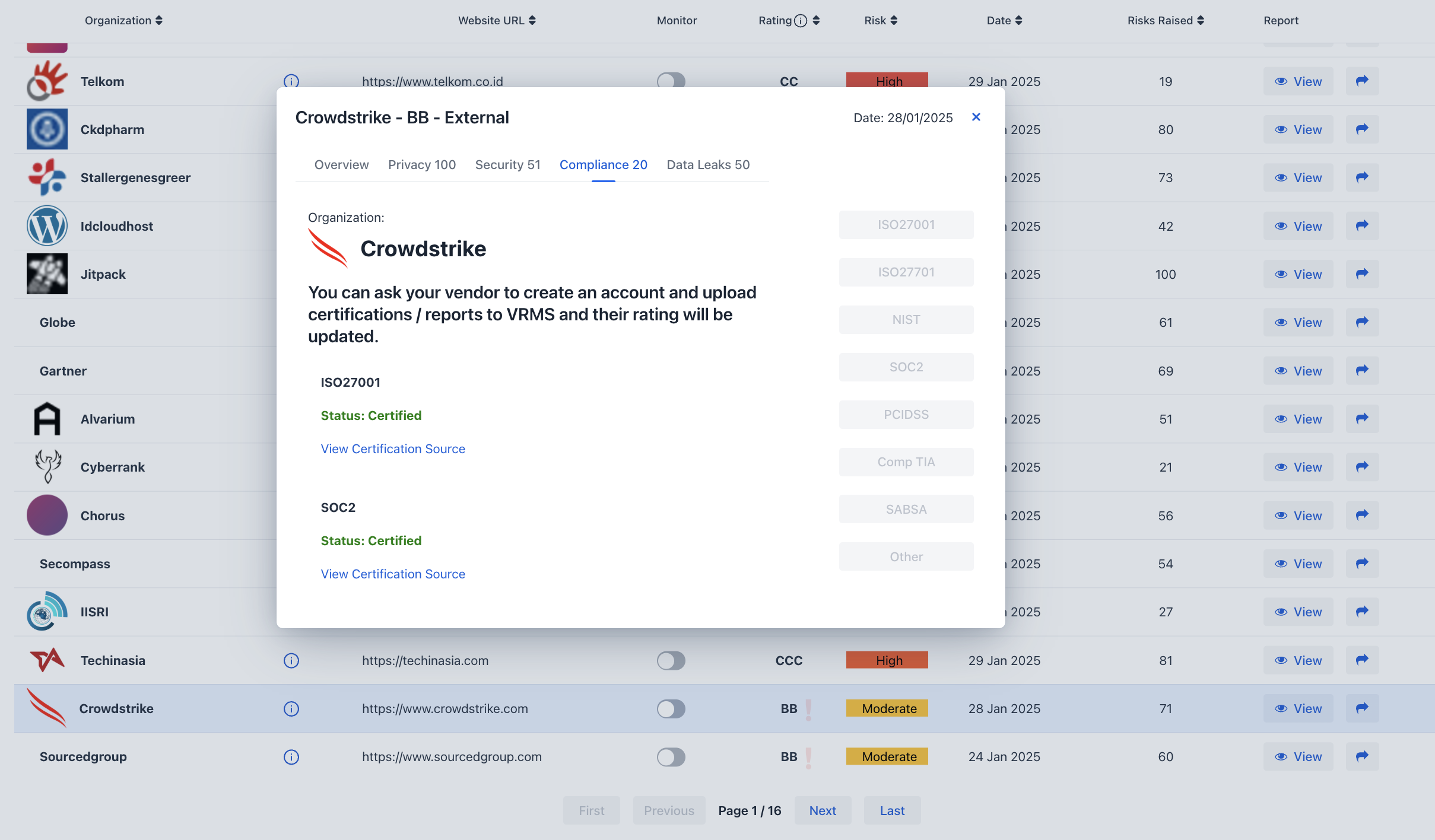
Vendors can upload compliance evidence, such as ISO 27001, SOC 2, DORA, and NIST reports, to validate their security standards.
CyberRank scans the internet to detect publicly available certifications and standards, including ISO 27001, SOC 2, DORA, NIST and others. If a certification is not published, vendors can upload their documents to CyberRank, where our team will verify their validity.
Yes, each reassessment incurs a cost of 20 credits.
CyberRank evaluates multiple factors, including security certifications, publicly exposed vulnerabilities, and recent incidents, to generate a comprehensive risk rating.
An exclamation mark will appear next to the rating, indicating a change in the company‘s security score.
Large organizations undergo daily sampling to provide real-time security insights.

We believe in making Cybersecurity accessible and transparent for everyone.
Login to CyberRank
CyberRank‘s is rooted in the IISRI® framework, built on years of auditing experience in the security and privacy sector.
IISRI®
Minimize third-party breaches and elevate your supply chain‘s cybersecurity posture with data-driven insights.
Login to CyberRank
IISRI® brings the Moody’s approach from finance into the cyber sector, providing ratings that assess the effectiveness of security and privacy controls. They evaluate performance, conduct audits, and develop solutions that make identity access management and third-party risk assessment both efficient and affordable.
IISRI®
By Onno W. Purbo - Institut Teknologi Tangerang Selatan (ITTS)
Complete mapping of Indonesian Data Protection Law requirements to technical controls and implementation strategies.
Over 94 million accounts affected by data breaches in Indonesia (2020-2023). Learn from actual incidents and prevention strategies.
Practical guidance on SIEM, DSPM, DLP tools with templates for audit-ready documentation and compliance reporting.
Step-by-step deployment guide from gap assessment to full compliance, including metrics and executive dashboards.
This book extensively features CyberRank as the optimal solution for Indonesian organizations seeking UU PDP compliance. With automated vendor risk management, continuous monitoring, and compliance-ready reporting, CyberRank simplifies the path to data protection excellence while reducing costs by up to 90%.
Critical Statistics
With 94.22 million accounts compromised in Indonesia between 2020-2023, and UU PDP mandating breach notifications within 3×24 hours with penalties up to 2% of annual revenue, comprehensive data privacy compliance is no longer optional—it's essential for business survival.