The Standard for
Security & Privacy Ratings
From AAA (Excellent) to D (Very Poor). Learn what each rating means for your vendor decisions. Our unique ratings cover both security AND privacy, something no other platform offers. Built by data protection experts based on international standards.
Get an Overview
Clear, high-level view of security and privacy risks.
Investment & Acquisitions
Check the risks related to any company before making important decisions.
Insurance Assessment
Determine premiums based on accurate risk assessment.
Benchmarking
Continuously improve your cybersecurity foundation.
The IISRI® Rating Scale
Explore our comprehensive risk assessment scale, from AAA (Excellent) to D (Very Poor).
↑ Click the bar to explore each rating

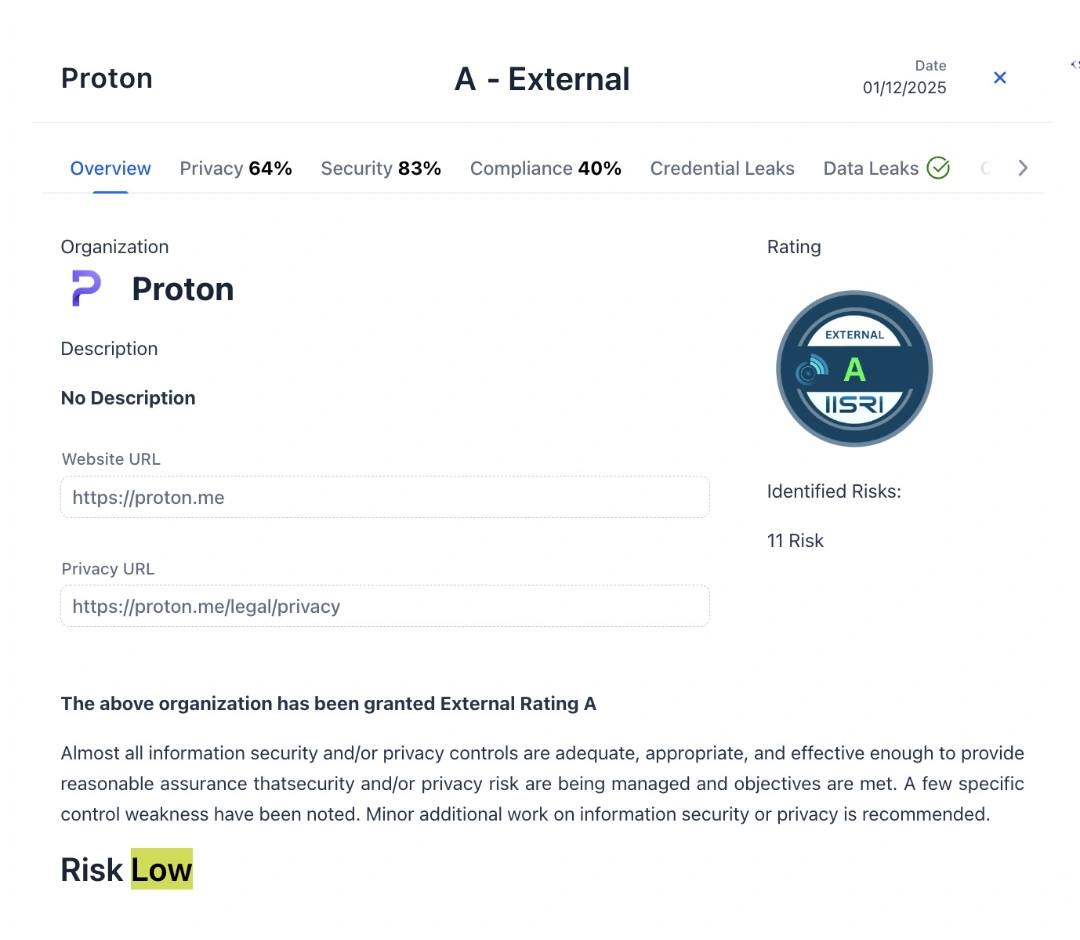
A Rating | Good
Almost all information security and/or privacy controls are adequate, appropriate, and effective enough to provide reasonable assurance that security and/or privacy risks are being managed and objectives are met. A few specific control weaknesses have been noted.
Action Plan

A Rating | Good
Almost all information security and/or privacy controls are adequate, appropriate, and effective enough to provide reasonable assurance that security and/or privacy risks are being managed and objectives are met. A few specific control weaknesses have been noted.
Action Plan
What Determines a Rating?
CyberRank analyzes five key areas using publicly available data, with no access to internal systems required.
Security Testing
Vulnerabilities on public-facing servers and subdomains.
Privacy Testing
Privacy policies, cookies, consent banners.
Compliance Detection
SOC 2, ISO 27001, HIPAA, PCI DSS detection.
Data Leak & Credential Detection
Breach database monitoring and exposed credentials.
Asset Discovery
All public-facing assets and subdomains.
CyberRank vs IISRI® Internal Ratings
Both use the same IISRI® rating scale (AAA to D). Choose the right approach for your needs.
CyberRank (IISRI® External)
Powered by AI & Public Data
Best For
IISRI® Internal
Comprehensive Assessment
Best For
Tip: Combine both for complete coverage. Start with CyberRank for quick external assessment, then use IISRI® Internal for deeper internal insights.
See Ratings in Action
Check any vendor's security and privacy rating or assess your own. Takes just 5-10 minutes.